Well architected network and security designs are essential for SAP Cloud Architectures on hybrid multi-cloud platforms with cloud computing and extensibility capabilities and cloud integration services. Cloud qualities like security or high availability have to be realized with network segmentation best practices, traffic controlling, load balancing, identity access management and data encryption implementations.
Architectural blueprints for Amazon AWS and Microsoft Azure cloud platforms intend to use similar components for virtual network segmentation with subnets and availability zones to ensure high availability based on independent data centers.
Network segmentation is typically implemented with private and prublic subnets. Workloads for web, application and database application tiers in private subnets can't be accessed directly from external and have no direct internet access. Public internet access of components within private subnets has to be routed to internet gateways of public subnets.
Enhanced traffic restrictions can be implemented with firewall capabilities, network security groups or routing tables.
Load balancers increase resilience, performance and availability of cloud architectures on different communication layers (OSI levels 3-7). They route traffic to targets with defined rules or based on health checks with layer specific communication protocols and transfer objects.
Application layer 7 requests can be routed using HTTP(S) with SSL offload based on application URLs or CDN origins (e.g. Azure Front Door CDN). DNS load balancer like Azure Traffic Manager or AWS Route53 offer high availability and failover capabilities for hybrid multi-cloud scenarios on presentation (OSI 6) or session (OSI 7) layers with geo-located routing.
Transport layer load balancers route traffic as TCP segments on OSI level 4 based on source or target IP address and port with availability zone support.
Active-Active cluster configurations support high availability with clusters of redundant workloads available for traffic routing.
Routing for Active-Passive clusters can use a priority routing method to route traffic to active regions unless this region fails.
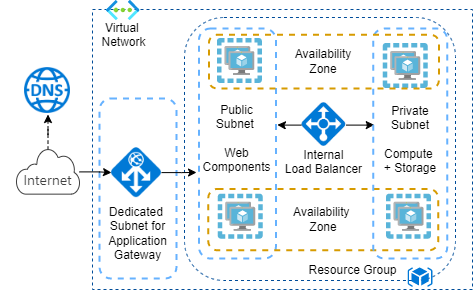
Azure Virtual Networks (VNet) are basic private network building blocks with own private IP address spaces. VNets are region specific assigned to one subscription and can segmented with subnets. Azure resources in subnets within virtual networks can communicate with each other via private IP addresses.
Azure VNet resources can reach per default the public internet via created default routes with IP address 0.0.0.0/0 and next hop type internet. Any traffic, not addressed to a specific range within the virtual network or as destination address of an Azure service, gets routed to the Internet.
With Virtual Network NAT configured on a subnet all outbound connectivity uses the static public IP addresses of the VNet NAT.
Azure Network Watcher provide tools to monitor network traffic within a VNet like IP Flow verify to find denied and allowed packages sent to or from a VM.
The Microsoft Azure Resource Manager allow to define network security components with infrastructure as code templates. Azure blueprints offer a declarative way to orchestrate the environment setup (deployment) of various resource templates on management or resource group level.
Availability Zones are geographically distributed locations with one or more data centers. Each region owns at least 3 availability zones to enable high availability with zone redundant workloads. Subnets span across availability zones of region.
Proximity Placement Groups group Azure compute resources, deployed in availability or virtual machine scale set, physically located as close as possible to each other to reduce latency.
Azure offers security groups and route tables to define rules and routes for traffic control like .
Network Security Groups (NSG) can be assigned to subnets or network interface cards (NIC) with a many-to-many relationship. Assigning NSGs to subnets is preferred with security rules applied to all NICs in the subnet. Subnet NSGs are processed first for inbound traffic, for outbound traffic NIC NSG rules are processed before subnet NSG rules.
NSG rules defined with source, destination, port and protocol offer basic firewall protection on OSI layers 3 and 4 for inbound or outbound traffic. Source and destination attributes have to be specified with VNet service tags like VirtualNetwork, Internet or Azure Load Balancer. Default NSG rules enable communication within the VNet, load balancer inbound and internet outbound, but deny all other external in-/outbound traffic.
Application Security can be grouped for applications running on servers (virtual machines) with the NIC assignment to Application Security Groups (ASG) like web (webASG) or database (dbASG) groups.
Azure automatically creates Route Tables for each subnet with system routes defined by address prefixes in CIDR notation and next hop types (e.g. Internet, Virtual Network). Custom routes can override system routes to route outbound traffic of subnets based on individual requirements or to limit the default internet access.
Outbound connectivity of virtual machines is enabled by default with public IPs owned by Azure, inbound traffic has to be enabled by assigning a public IP address or load balancer. The default outbound connectivity should be replaced for production workloads explicitly created public IP addresses or NAT Gateways.
Azure VNet Service Endpoints secure and direct connection to Azure services through an optimized route within the Azure backbone network. They limit and protect services without additional charge. For internal service traffic the access to resources switches to private IP addresses of the virtual network.
Azure VNet Peering connects virtual networks with each other also enables communication of resources across the VNets.
Azure Private Link enable access to Azure PaaS services, customer or partner services hosted on Azure with a private virtual endpoint and traffic over the Microsoft backbone network. Private Link introduces a private IP for a given instance of the PaaS Service. The service gets accessed via the private IP from peered VNets or on-premise networks.
Point-to-Site VPNs are connections between local single computer and Azure virtual networks.
Azure Site-to-Site VPNs are connections between local VPN device and VPN gateway deployed in VNet. Forced Tunneling redirects all internet-bound traffic back to your on-premises location via a Site-to-Site VPN tunnel for inspection and auditing.
Azure ExpressRoute Circuits are private connections between local networks and Azure or Office 365, using Layer 3 connectivity with Border Gateway Protocol (BGP). ExpressRoute circuits can be cross connected to multiple peered VNets.
Microsoft Azure offers load balancing options for different OSI communication layers.
Azure Application Gateways are web traffic application load balancer (OSI layer 7) which allow routing based on URLs or HTTP request attributes, support SSL termination and round robin routing for traffic load balancing. Web Application Firewalls (WAF) protect against common vulnerabilities and exploits like SQL injection attempts, XSS, DDoS
Azure Load Balancer (basic or standard) distribute incoming internet TCP / UDP traffic on OSI tranport layer 4. Standard load balancer with two healthy endpoints support high-availability with 99.99% SLA. Public load balancers provide outbound connections with endpoints for VMs or VMSS. Internal load balancers provide private IPs, but can also be accessible in hybrid scenarios from on-premise.
Azure Traffic Manager is a DNS based load balancer which offers high availability and responsiveness for service endpoints across regions. Domain names can represent multiple IP addresses and routing methods have to determine the target IP address for a specific client request.
The Azure Traffic Manager monitors the health of endpoints with threshold settings and decides based on defined limits when to fail over to passive regions. Traffic routing methods follow strategies like e.g. priority settings, defined weights, performance with lowest latency or geographically closest.
Standardized best practices for Amazon AWS network security architectures can be implemented as infrastructure as a code with CloudFormation templates for network and security components. The following diagram visualizes the components of a Amazon AWS default VPC.
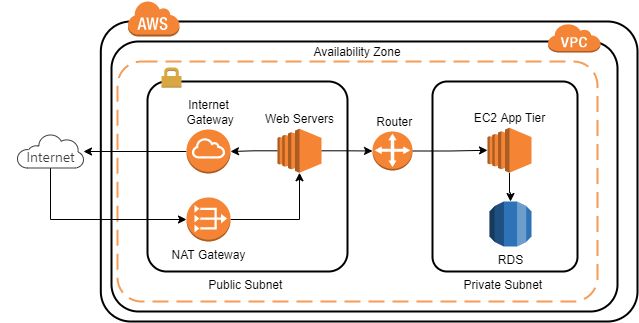
Virtual Private Clouds (VPC) are logically isolated virtual networks on AWS accounts with ranges of IPv4 addresses as CIDR block. VPC span over all (at least 3) availability zones of a region.
AWS Subnets separate public external-facing network segments from private segments for internal resources. Each subnet must reside entirely within one availability zone.
AWS Local Zones reduce latency and allow to fulfill data residency requirements with portions of application local to end users or resources.
Traffic within AWS VPC can be controlled on differently on network, subnet or instance levels. VPC NAT gateways enable outbound internet access for instances in private subnets, but protects against public internet access with better availability and bandwidth than NAT instances. Routing Tables, associated with subnets or gateways (VPN, Internet), direct traffic with routes within VPCs.
Network Access Control List (NACL) act as firewall to control inbound and outbound traffic on subnet level. Per default all ports (in-/outbound) are open and configuration is done with rules (allow/deny). The return traffic has to be explicitly allowed (stateless behavior) with random ports from the ephemeral port range (1024-65535) as client source port.
AWS Network Security Groups implement firewall protection on EC2 instance level. All inbound traffic from other hosts is denied and all outbound traffic is allowed by default. Security group rules are always permissive, with filters for protocols and ports. The stateful behavior allows response in-/outbound traffic after allowed out-/inbound traffic.
AWS offers elastic load balancing to targets deployed in availability zones on OSI communication layers 3-7 with four load balancer types.
Application Layer (OSI 7) HTTP request routing can be implemented with AWS Application or Classic Load Balancers. Transport layer (4) routing of TCP segments is available with Network (4), Gateway (3/4) and Classic (4) load balancers. OSI network layer (3) routing of network packets with IP route tables is supported by AWS Gateway Load Balancers.
Secure networks on hybrid multi-cloud platforms shall be realized with multi layered Defense in Depth strategies implementing security best practices with cloud services of hyperscaler platforms like Azure or AWS.
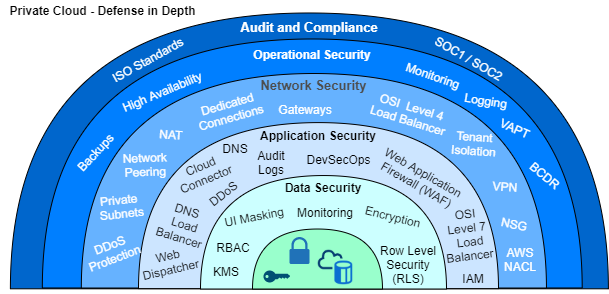
Virtual network peering enables secure connections with private traffic on hyperscaler backbone networks without the need of public internet, gateways and encryption.
Some DDoS (Distributed Denial of Service) attack examples on different OSI layers are listed below:
| OSI Layer | DDoS Attack Vector Example |
|---|---|
| Application (7) | HTTP, DNS query floods |
| Presentation (6) | TLS abuse |
| Transport (4) | SYN floods: client sends large number of synchronization (SYN) packets, server acknowledges (SYN-ACK), but client doesn't complete handshake with ACK |
| Network (3) | UDP reflection attacks: client sends request to intermediate server which forwards an amplified, several times larger response to attacked servers |
Hyperscaler services to protect against DDoS attacks are:
| Protection Layer | Azure Services | AWS Services |
|---|---|---|
| Layers 3-4 | Azure DDoS Protection | AWS Shield |
| Layers 6-7 | WAF (Traffic Manager, Front Door) | WAF (Route 53, CloudFront) |
Cloud data security strategies have to be implemented for data in rest and transit on multiple OSI (Open System Interconnection) layers.
Cloud providers implement different data encryption strategies for network traffic:
Cloud customers are responsible to encrypt data in transit on application level (OSI layer 7) by using TLS (SSL) with TLS handshakes to establish sessions (OSI layer 5) for encrypted communication (OSI layer 6).
Services to manage secrets, certificates or keys, with custom key management (BYOK - bring your own key) strategies like AWS KMS or CloudHSM, AWS SecretsManager, Azure Key Vault or SAP BTP Credential Store.
Dynamic Data Masking prevents unauthorized access to sensible data in databases like e.g. SAP HANA, Azure (SQL Database, SQL Managed Instance, Synapse Analytics) or AWS Redshift. Implement Row Level Security to control database row access with rules.
Cloud IAM solutions manage digital entities of cloud-based software services (SaaS) to ensure compliant processes in hybrid multi-cloud environments.
Some IAM security areas are Identity Governance, Provisioning and Federation.
AWS Config and Azure Resource Graph enable continuous monitoring and assessment of resource configurations. AWS Organizations and Azure Policies help to enforce organizational standards and to assess compliance.
Vulnerability Assessment Penetration Testing (VAPT) improves cloud security and helps to identify cyber security vulnerabilities.
Azure AD (AD) is a cloud Identity Access Management (IAM) solution to store information about users, groups and applications for OAuth, SAML or OICD based authentication. Azure AD offers in contrast to on-premise AD application management but no domain services. One Azure AD tenant is associated with one Azure subscription.
Some important features of Azure AD:
Microsoft provides on-premise and cloud Domain Services:
The Microsoft Identity Management offers different possibilities to implement access control. Service principals and managed identities enable tool based access to Azure AD secured resources.
Examples are Terraform which offers authentication options via Managed Service Identities, Service Principals (with client certificate, secrets or OIDC) or Azure CLI to implement infrastructure as a code. Argo CD and Workflows can be configured via App Registration (Dex, OIDC) or Enterprise App (Dex) for Azure AD authentication.
Azure AD assigns Service Principals in the enterprise application area to external applications (like SAP IAS, Dex as Azure AD proxies) or Azure Portal applications, registered with an Application (client) ID in the App Registration.
Resources can access other resources, secured by Azure AD authentication with managed identities, which are a special kind of service principals. Managed identities can be created system-assigned to one specific resource or user-assigned outside the resource creation process. Virtual Machines request access tokens from the Azure Instance Metadata Service (IMDS) for their managed identities to access Azure services like Key Vault.
On-Premise applications can be integrated with Application Proxies as Azure AD Enterprise Applications with security features like Conditional Access or MFA.
Shared Access Signatures (SAS) offer time limited, fine grained access control to resources.
Role based access control (RBAC) is an authorization system based on Azure Resource Manager (ARM). Owner and Contributor built-in roles allow full access to manage resources. Owner and User Access Administrator roles enable to grant access to others. Custom roles can grant or deny access on management group, subscription, resource group or resource level to users, groups, services or principal identities. DevTest Lab users have view access and DevTest owners can additionally modify e.g. policies, VMs or virtual networks.
Azure Policies are used to implement governance, to enforce organizational standards, to assess compliance with resource properties checks and enable to apply alerts e.g. when new subscriptions are added. Policies can be assigned on management group, subscription or resource group level.
The table below offers some basic information about AWS services for Single Sign On (SSO) and Identity Authentication Management (IAM).
| Service | Short Description |
|---|---|
| AWS SSO
allows to centrally manage access to multiple AWS accounts or cloud
business applications like Salesforce. AWS SSO provides users single
sign-on access to all their assigned accounts and applications.
AWS SSO supports automatic provisioning (synchronization) of user and group information from Azure AD. AWS SSO can be integrated with Microsoft AD using the AWS Directory Service. |
|
| AWS Directory Service (AWS Managed Microsoft Active Directory) extends your on-premises Microsoft Active Directory domain to the cloud without the need to synchronize or replicate data | |
| AWS Cognito secures access to applications with user pools, which can be integrated with external ID providers like Facebook or Google | |
| Identity Access Management (IAM) grants access to AWS services and resources with execution roles and policies within an AWS account | |
| Lambda Authorizer is a API Gateway feature that uses Lambda function to control access to your API with a bearer token authentication strategy such as OAuth or SAML |
Encryption together with key management are important features to secure workloads and store data confidential in multi-cloud environments. Customers can use BYOK (Bring your own key) and BYOE (Bring your own encryption engine) features to keep full control over the encryption.
Azure supports various encryption models with client-side encryption outside of Azure, customer managed keys or server-side encryption.
Encryption is one layer of the AWS defense-in-depth security strategy. With KMS and CloudHSM services, you can store data and keys separately at rest. TLS is used to encrypt data in motion.
AWS KMS is a multitenant Key Management Service, managed by AWS, to create and manage cryptographic keys and with usage control.
AWS CloudHSM is under full customer control in a separated VPC, and allows to generate and use own encryption keys in the AWS Cloud.
SAP hybrid multi-cloud environments shall follow security best practices, standards like ISO/IEC and regulations like GDPR or BSI Cloud Computing with shared responsibilities for customers and cloud providers. GDPR (General Data Protection Regulation) defines shared responsibilities for personal data processing between data controllers, which determine means and purposes, and data processors, processing data on behalf of data controllers.
Customers act as GDPR data controllers and have to implement security on different levels with application related responsibilities:
Customers have to define secure processes which follow legal requirements with reviews of application logs and third party audit logging of personal data access. They have to implement data life cycle requirements and data protection with access and change control. Hybrid customer cloud environments shall be connected securely between on-premise and cloud.
Cloud providers act as GDPR data processers with responsibilities for system level security like separation of tenant data and encryption of data on rest or transit. Secure cloud provider data centers have to implement redundancy of critical components (like two separately connected power supply grid sectors), monitoring of key work components (e.g. cooling or power supply), multiple firewalls to divide networks into protected segments and multiple internet connections to minimize the impact of distributed denial-of-service (DDoS) attacks.
RISE S/4HANA Cloud security management is supported by tools like: